Good afternoon,
Yesterday our MGMs running version v5.2.24 have been successfully migrated to Alma and EOS v5.2.26.
However, we encountered an issue with the secondary groups which were not loaded any more when the users were authenticated (using Kerberos), meaning they were only considered part of their primary group so were now denied access to many folders.
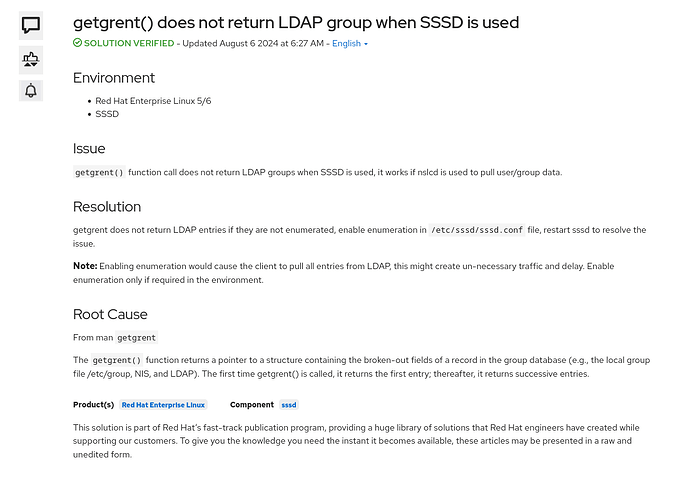
We have been running for years with this configuration in CentOS, where the users and groups are defined in an LDAP directory, which is brought to the OS by the nslcd service which connects to LDAP. In Alma9, this task is now handled by more modern SSSD equivalent. In the EOS configuration, we checked of course that we still had the necessary EOS_SECONDARY_GROUPS environment variable.
We finally found that the reason was due to a parameter in the sssd configuration in our domain definition,enumerate=false which disables the possibility to list the whole groups or users (using getent passwd or getent group fro instance), and seems a default and recommended setting for sssd.
So first question is : is there a reason why EOS needs this enumerate option to be enabled ? When running a id user command in the host, all the secondary groups are correctly shown, so we thought it would be sufficient to make the same query for the user when he is authenticated. And also, if EOS enumerates all users/groups, is there a limit in the number of groups it can retrieve from the LDAP ? What if we have many many groups?
When changing this setting, and restarting SSSD and invalidating its cache, then for users who authenticate the first time, the groups were immediately loaded. But for users authenticated previously, this was not the case immediately, unless the MGM is restarted, or we wait enough : it appeared that after around 1 hour all the user information were updated at once, and the issue disappeared. As if indeed all the group information was reload at the same time.
Second question is : is there a way we can force cache invalidation of user and groups information in the MGM ? It would have ben helpful in this exceptional case, but we also observed several times even under CentOS 7 that adding a user to a group takes some time to be taken into account, and sometimes requires that the user logs out completely before it is updated.
Maybe there are some recommended settings to work optimally in this situation that we might apply to our configuration ? Thank you to anyone who can share his experience.
Additional note : In the past, we had the issue with secondary groups missing in the gateway mode, but we noticed that in some previous update (maybe version 5+) it was improved, thanks